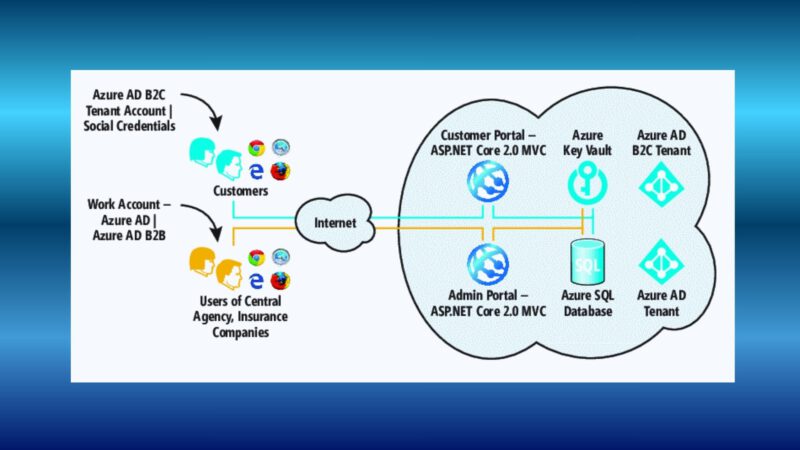
Creating an Azure KeyVault may seem simple, but a truly secure configuration requires more than just clicking “Create.” In this complete guide, I will walk you through the entire process step by step, including:
As organizations move more and more workloads to the cloud, it becomes increasingly clear that handling sensitive data securely is no longer a luxury but an absolute requirement. That’s why creating an Azure Key Vault is a logical and strategic first step toward a modern security architecture. On one hand, Key Vault provides a central location where secrets, keys, and certificates can be stored securely. On the other hand, its deep integration with Microsoft Entra ensures that access is always identity‑based, eliminating traditional risks such as hard‑coded passwords.
Additionally, Azure Key Vault enables organizations to standardize and automate security, which not only increases protection but also significantly improves operational efficiency. Features such as auditing, versioning, and network isolation help organizations meet increasingly strict compliance requirements. In short, anyone serious about Zero Trust and secure automation simply cannot ignore the importance of creating an Azure Key Vault.
- Resource group structure
- VNet design
- Private endpoint configuration
- Private DNS zone
- Firewall settings
- Security and management best practices
This guide follows Microsoft best practices for maximum security.
Why creating an Azure KeyVault with a private endpoint?
A Key Vault contains sensitive information such as:
- API keys
- Secrets
- Connection strings
- Certificates
You want to prevent these from being accessible over the public internet. With a private endpoint, your Key Vault is only accessible through your own Virtual Network (VNet). This is the safest and recommended approach.
Step 1 — Prepare resource groups
Use a clear separation between security and networking:
| Resource | Recommended RG |
|---|---|
| Key Vault | RG‑Security |
| VNet + subnets | RG‑Networking |
| Private endpoint | RG‑Networking |
| Private DNS zone | RG‑Networking |
This structure prevents accidental deletion of your Key Vault and simplifies RBAC management.
Step 2 — Creating a Virtual Network for the Azure KeyVault
Go to: Azure Portal → Virtual Networks → Create
Use:
- Address space: 10.0.0.10/16
- Name: vnet-keyvault
- Resource group: RG-Networking
- Region: same region as your Key Vault
Add a subnet for private endpoints:
- Subnet name: snet-private-endpoints
- Subnet range: 10.0.1.0/24
This subnet is exclusively for private endpoints.
Step 3 — Creating an Azure KeyVault
Go to: Azure Portal → Key Vaults → Create
Fill in:
- Resource group: RG-Security
- Name: choose a unique name
- Region: same region as your VNet
Then go to the Networking tab.
Step 4 — Configure Networking (important!)
Under Networking, choose:
- Selected networks
- Public access: Disabled
- Allow access from: Private endpoints only
This ensures your Key Vault is not reachable via the internet.
Scroll to Private endpoint connections → click Add.
Step 5 — Creating the private endpoint for an Azure KeyVault
In the wizard:
Basics
- Resource group: RG-Networking
- Name: pe-keyvault
Resource
- Resource type: Microsoft.KeyVault/vaults
- Select your Key Vault
Networking
- Subnet: snet-private-endpoints
- Virtual network: vnet-keyvault
Step 6 — Creating the link the Private DNS Zone for an Azure KeyVault
Under Private DNS integration:
- Integrate with private DNS zone
Azure automatically creates the correct zone:
- privatelink.vaultcore.azure.net
This ensures that <yourvault>.vault.azure.net resolves to the private IP of your endpoint.
Step 7 — Security best practices
- Use Azure RBAC for access
- Enable Soft Delete and Purge Protection
- Use Managed Identities instead of secrets
- Monitor access via Azure Monitor and Activity Logs
- Use Key Rotation for certificates and keys
Step 8 — Creating a key and value in the Key Vault
You want to create a secret in Azure Key Vault with:
- Value: your actual client secret (e.g., from Business Central On‑Prem)
- Name: ClientSecret-BC-OnPrem
Requirements:
- Key Vault Secrets Officer or Key Vault Administrator role
- A Key Vault (preferably with a private endpoint)
- Access via Azure RBAC or Access Policies
- Your client IP whitelisted in the Key Vault’s Networking settings
Step 1 — Go to your Key Vault
- Open Azure Portal
- Search for Key Vaults
- Click your Key Vault (e.g., kv-security-prod)
Step 2 — Go to Secrets
In the left menu:
- Objects → Secrets
- Click: + Generate/Import
Step 3 — Configure the secret
You now see a form with fields.
Secret type
- Leave on: Manual
- Enter: ClientSecret-BC-OnPrem
Value
- Enter the actual client secret, e.g.:
<your-client-secret>
Step 9 — Test whether your Key Vault is privately reachable
You can use PowerShell for this. These steps are done in Visual Studio Code.
Install-Module Az.Accounts -Scope CurrentUser
Install-Module Az.KeyVault -Scope CurrentUser
Connect-AzAccount
$secret = Get-AzKeyVaultSecret -VaultName "My-KeyVault-WEU" -Name "ClientSecret-BC-OnPrem"Conclusion — Creating an Azure Key Vault
With these steps, you now have a fully secured Azure Key Vault:
- Not publicly accessible
- Only reachable via private endpoint
- Correct DNS integration
- Clear resource group separation
- Fully aligned with Microsoft best practices
For what it is worth
This is how professional cloud architectures securely manage their secrets. Ultimately, creating an Azure Key Vault is a crucial step toward a modern, secure, and future‑proof cloud environment. On one hand, Key Vault provides a central, highly secure platform for storing secrets, keys, and certificates. On the other hand, the combination of network security, RBAC access, and Microsoft Entra integration enables organizations to truly apply Zero Trust principles.
Using Key Vault also simplifies the management of sensitive data, eliminating the need for hard‑coded passwords or insecure configuration files. Features such as versioning, auditing, and automatic rotation help you work not only more securely but also more professionally and consistently.
In short, by creating and correctly configuring a Key Vault — including network access, firewall rules, and role assignments — you lay the foundation for secure automation and reliable cloud architecture. This leads to fewer risks, less administrative overhead, and significantly more control over your security landscape. In other words: an Azure Key Vault is not a luxury, but an absolute necessity for any organization serious about security and automation.
You can find more information about Key Vaults here.
You can contact me via this form.